Posted originally on the CTH on December 28, 2022 | Sundance
In the background of international geopolitics and all things economically attached, the larger climate change agenda, the Build Back Better program, has been unfolding.
Energy driven inflation has destabilized most western economies as the various governments (politicians) and central banks (bureaucrats) work together on behalf of the corporations (World Economic Forum). All of these interests can only advance if they work together. If any individual nation breaks from the group energy agenda, their economy will thrive beyond the limits created by the BBB operation and the association of western nations.
It is with this context at the forefront where we have said to watch Mexico closely. In North America, Mexico has the least to gain from economics behind the climate change agenda. Conversely, if Mexico were to go rogue, they would gain the most. This dynamic puts Mexico in a more powerful position than most realize.
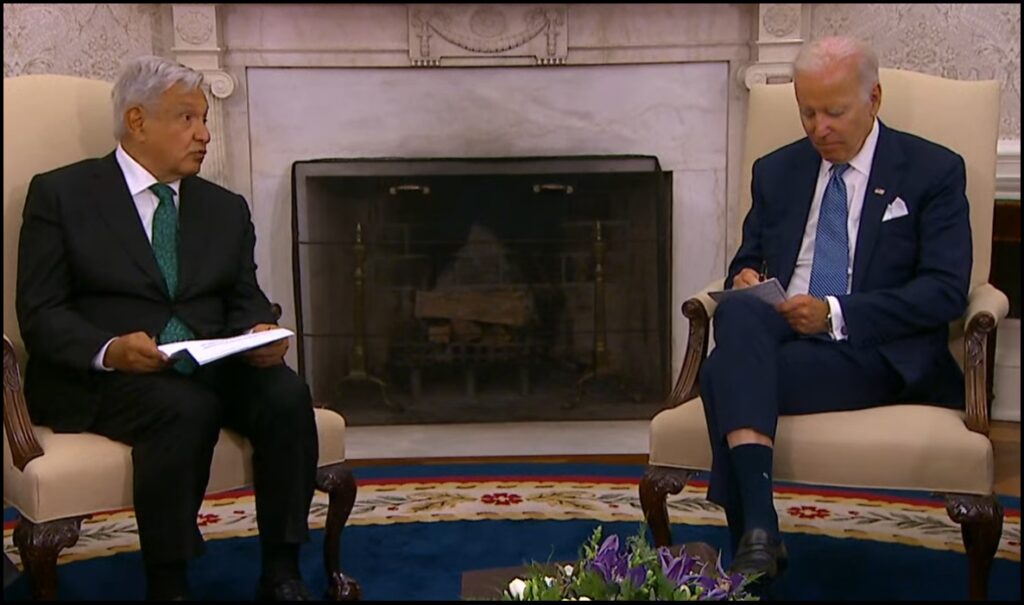
During a July 2022, meeting at the White House, Mexican President Andres Manuel Lopez-Obrador (AMLO) appeared to indicate -for the first time- his understanding of his new position as the ‘Green New Deal’ (climate change) energy agenda was being deployed by the U.S. and Canada. AMLO read from a prepared script in the oval office during a public bilateral meeting with Joe Biden. AMLO’s remarks were quite remarkable in their independence.
“In our country, we shall continue producing oil throughout the energy transition. With the U.S. investors, we are going to be establishing gas-liquefying plants, fertilizer plants, AMLO said, striking a chord that is not in alignment with Joe Biden and Justin Trudeau. AMLO continued, “and we’re going to accomplish this with the support of thermal electric plants and also through transmission lines to produce energy in the domestic market, as well as for exports, to neighboring states in the American union, as for instance, Texas, New Mexico, Arizona, and California.” It’s not just what he said, it’s how AMLO said it.
Keep in mind, the month before that July visit to the White House, AMLO boycotted Joe Biden’s Latin-America Summit. AMLO joined the leaders of Bolivia, Guatemala, Honduras and the tiny Caribbean state of St. Vincent in refusing to attend the Biden summit because Cuba, Venezuela and Nicaragua were blocked from attending by the Biden administration.
Socially and ideologically AMLO is a soft-socialist (immigration). However, he is also a strong economic nationalist who has previously expressed a dislike for the influence of multinational corporations in Mexico. As an outcome of his worldview, AMLO is not in alignment with the World Economic Forum. This is why we have said to watch Mexico in 2023; the dynamic will be very interesting.
Joe Biden and Justin Trudeau are in alignment with a North American approach toward energy, AMLO is the outlier. The people behind Biden and Trudeau also appear to want a North American Union established, essentially a nationless and borderless North America. On that aspect AMLO may be in agreement. However, watch for the key word “equity” in these discussions. Mexico is the poorest house on the block and if Canada and the United States want to create a unified North America, AMLO will want the Mexican people to be the biggest economic beneficiaries.
MEXICO – At today’s morning press conference headed by President Andrés Manuel López Obrador, Foreign Secretary Marcelo Ebrard presented the agenda for the tenth North American Leaders’ Summit (NALS) and its related meetings. The Summit will be held on January 10 in Mexico City.
The Foreign Secretary said that bilateral meetings will be held during the Summit. “The bilateral meeting between Mexico and the United States will include […] a wide range of actions focused on bilateral trade and investment, and on speeding up the border infrastructure projects.”
“Bilateral cooperation issues will be addressed, such as migration […] labor mobility, trade, security, education, culture, combating climate change… Labor mobility has already been added to the dialogue, the narrative, and the concept of the relationship between Mexico and United States. This did not exist [previously]; this is very recent […] Both the agreement we reached with Secretary Kerry, which was announced in Egypt […] on clean energy, […] and the Sonora Plan will be presented. The goal is for this dialogue to strengthen the integration of regional supply chains and the transition towards electromobility and clean energy.”
The Secretary said that, in the National Palace, the Summit tentatively includes “a private segment between the three leaders, that is, a conversation between the three of them, and then we will have an extended meeting with the delegations of each of the three countries.”
He mentioned the six main topics that will be addressed at the summit: diversity, equity and inclusion; the environment; competitiveness with the rest of the world; migration and development; health; and shared security.
“The three nations will seek to continue the process of regional integration, based on the principles of respect, sovereignty and good faith cooperation for mutual benefit; that is the goal,” he said.
The Foreign Secretary also announced that there will be a bilateral meeting between Mexico and Canada between President López Obrador and Prime Minister Trudeau. “They are going to talk about both governments’ strategy for indigenous peoples and historically marginalized communities. This is a topic that both Minister Trudeau and President López Obrador have promoted. There is a lot of international interest in this, in what has been done with the Yaquis and with other indigenous peoples of Mexico.”
The Foreign Secretary said that, at the Summit, “One of Mexico’s most important priorities relates to the actions that must be taken in 2023-2024 to reduce the poverty and inequality that are growing in the Americas […] this is the most important priority from the Mexican perspective.”
“We are going to propose a Partnership for the Prosperity of the Peoples of the Americas […], this is what President López Obrador discussed with former Senator Dodd on his recent visit, and the Canadians have also been consulted,” he said, adding, “The main goal (of the partnership) will be to fight poverty and achieve a more equal distribution of resources in the Americas based on strengthening the trade relations and relations of all kinds on the continent […] so that North America remains a leading economic power at a global level, which would make it possible to establish new ties with the rest of the continent, based on mutual respect,” he concluded. (Read More)
President Lopez-Obrador has all the power in this dynamic right now.
AMLO is using the western energy transition to keep himself in a position of economic strength. In order to pull AMLO into the western climate change energy program, Biden and Trudeau will have to bribe him with major economic incentives; essentially, promises and economic outcomes to close the wealth gap.
If Mexico goes rogue, their economy can skyrocket. However, if Mexico goes rogue, the people behind Biden will destroy AMLO (Brazil exists as a reminder to him).
The U.S. and Canada are going to push every possible political pressure point in order to force Mexico to change energy policy. The stakes are high. It is going to be remarkable to watch what happens as this battle takes place.
Watch Mexico in 2023.