Posted originally on Rumble By Bannons War Room on: May 8, 2024 at 07:00 pm EST


This is more than a little interesting and aligns with my own research and discussions. House Speaker Mike Johnson was lobbied by former CIA Director Mike Pompeo and current officials from the CIA, DNI and Intelligence Community.
This effort, and his son starting at the Naval Academy, is what changed Johnson’s mind about allowing the U.S. intelligence community to have his full support in the IC war against the American people.
The story is shared by CNN, the official outlet for perspectives and viewpoints held by the U.S. State Dept (CIA), so keep the narrative origination in mind. Here are the key points as written in the article:
WASHINGTON – […] The speaker’s embrace of Ukraine aid represents a remarkable evolution for Johnson, who voted against funding for the country as a rank-and-file member. But almost immediately after securing the speaker’s gavel, sources say he began to hear directly from critical Republican national security voices – including Donald Trump’s former secretary of state, Mike Pompeo, who impressed upon him the urgent need to approve assistance for Ukraine in its fight against Russia’s invasion.
In March, Ukrainian President Volodymyr Zelensky lobbied the speaker directly. Within minutes of the House approving a new military aid package for Ukraine on Saturday, Zelensky offered his thanks to US lawmakers, and in particular to Johnson for his decision that “keeps history on the right track.”
And more recently, Johnson received a key intelligence briefing from CIA Director Bill Burns, who painted a picture of the dire situation on the battlefield in Ukraine and the global consequences of inaction, according to multiple sources with knowledge of the situation. The briefing left a lasting impression, and Johnson became increasingly convinced the fate of Western democracy was on his shoulders, sources close to him said.
Another factor that sources say weighed heavily on his decision-making: Johnson’s oldest son was recently accepted into the Naval Academy.
“To put it bluntly, I would rather send bullets to Ukraine than American boys. My son is going to begin in the Naval Academy this fall. This is a live-fire exercise for me as it is so many American families,” Johnson told reporters. (read more)
♦ The U.S. Intelligence Community (USIC) is at the epicenter of all modern corrupt politics. Every element of weaponized government, each example of action taken, can be traced to an agency within the USIC.
Similar to every other person I have ever met in Congress, House Speaker Johnson was pressured by the USIC and accepted their position. Johnson then changed his mind on the priorities of the USIC, sided with them in everything they requested, and pushed all he knew about the corrupt and weaponized conduct of the USIC to the side.
Keep in mind, we know the core ideology of the USIC is political and corrupt. We also know the core motives of the USIC are weaponized against anything that would remove their power tentacles from control. We know this, because the former USIC Inspector General was an institutionally corrupt guy named Michael Atkinson.
Before becoming the Intelligence Community Inspector General (ICIG), Michael Atkinson was the chief legal counsel at the DOJ National Security Division. Atkinson was the office lawyer for the Deputy AG in charge of the DOJ-NSD. Essentially, Atkinson was the internal compliance officer within the DOJ-NSD responsible for making sure all the rules and regulations of the national security division were maintained and accurate.
Michael Atkinson was Acting DAG Mary McCord’s lawyer when she was head of the DOJ-NSD, and when she submitted the fraudulent Title-1 FISA warrant against Carter Page that was used as a surveillance tool against Donald Trump and his campaign.
Atkinson would know the granular details of the FISA application, because it was his job at the DOJ-NSD to audit every U.S. Attorney Office that submitted FISA applications – including Washington DC.
When Mary McCord left the DOJ-NSD, she went to work for Adam Schiff and Jerry Nadler on the joint House committee to investigate Donald Trump. When Michael Atkinson left the DOJ-NSD, he went to work as the Intelligence Community Inspector General.
It was Atkinson who changed the rules allowing an anonymous whistleblower in the CIA (Eric Ciaramella) to make accusations against the office of President Trump. Whistleblower Ciaramella previously worked for Joe Biden when the corrupt Burisma business venture with Hunter Biden in Ukraine was set up.
Atkinson set up the system for Ciaramella to make an accusation against Trump, while keeping Ciaramella’s name hidden. This previously not permitted secrecy stopped the general public and DC people from knowing the background political motives of the claim against Trump by hiding Ciaramella.
The combination of Michael Atkinson’s work in the DOJ-NSD (Page FISA warrant), and the work he then did to set up the fraudulent CIA claims against President Trump (with Eric Ciaramella), stands as irrefutable evidence of the corrupt and weaponized activity by the Intelligence Community Inspector General. This shows how the IC is corrupt/weaponized.
The cherry on the proverbial corruption cake happened when ICIG Michael Atkinson helped construct the fraud against Trump; he then turned over all the fake whistleblower evidence to the Shiff/Nadler committee. The head of that committee was Mary McCord, Atkinsons former DOJ-NSD cohort. In essence, Atkinson gave McCord another fraudulently constructed set of documents to attack Donald Trump.
The first time McCord and Atkinson worked together, it was to conduct surveillance of Donald Trump and then hide the evidence. The second time Atkinson and McCord worked together, it was to impeach Donald Trump and then hide the evidence.
I hope everyone can see how the embeds within the Intelligence Community are completely political and working diligently to retain and operate a weaponized system. The functionaries deeply inside the mechanisms of the intelligence apparatus are the ones doing this; it’s not just the heads of the executive agencies as appointed by the Obama/Biden administration.
♦ MAIN POINT – The Intelligence Community overall is corrupt – soup to nuts. If the IC was not comprehensively corrupt, someone like ICIG Michael Atkinson could never become inspector general.
Now…. think about everything that stems from the outcomes of the Intelligence Community!! Everything about everything the IC puts into the DC system; everything that creates policy and executive/legislative action is politically motivated and corrupt.
It’s not just about renewing FISA-702 surveillance on Americans, it’s everything.
THINK!
Think about wars, borders, national security, threats domestically, threats ignored/downplayed due to ideological makeup of the IC. Instructions given to politicians, briefings to the President, advice to policymakers, positions of military assets, foreign policy, election security, DHS mandates, border impacts, and so much more.
Meanwhile, the judicial branch defers to the IC on all matters of national security. Think about the ramifications.
It’s not hard to see how fully collapsed our system is once you realize how fully corrupt the intelligence apparatus has become.
Posted in 1st Amendment, 4th Amendment, A New America, Abusive Cops, Activist Judges, Big Government, Big Stupid Government, Cold Anger, Decepticons, Deep State, Dept Of Justice, DHS, Donald Trump, Election 2024, Lawfare, Legislation, media bias, Notorious Liars, NSA, Patriotism, President Trump, propaganda, Spygate, Spying, Typical Prog Behavior, Uncategorized, USA, White House Coverup
The Fourth Amendment to the United States Constitution says: “The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.”
Late last night, early this morning (after midnight), the United States Senate passed a FISA reauthorization bill that directly and specifically violates every tenant of the 4th Amendment.
The Senate voted to authorize warrantless federal government searches of every American’s private papers, effects, emails, electronic data records, cell phone calls, contact lists, text messages, buying habits, purchases, banking records, social media posts, direct messages, private communications and every keystroke of every electronic device in your life. All of it continues to be subject to the capture, review and surveillance of an unelected opaque law enforcement mechanism, and Congress supports it.
The issue is magnified, because the Supreme Court has never ruled on the constitutionality of the FISA-702 data collection system, because the Supreme Court also says no American has standing to challenge the federal government violation of their 4th Amendment right to privacy. It’s all infuriating… It’s all FUBAR!
Oh, and if you are reading this… you’re likely on the list.
Last night, Senator Dick Durbin (D-IL) teamed up with Sen. Kevin Cramer (R-ND) and added an amendment that would have required the government to get a warrant before reviewing any communications incidentally collected from Americans. The amendment was the last effort priority for a smidgen of hope; the IC railed against it, saying it would stop them from acting on critical “national security” information in real time. It failed by a vote of 42 to 50.
Another Democrat Senator, Ron Wyden (Oregon), a senior member of the Senate Select Committee on Intelligence, vowed and pledged that FISA-702 would never be renewed by any measure that required his signature. “I’ll do everything in my power to stop it,” he previously said. “Searches have gone after American protesters, political campaign donors, even people who simply reported crimes to the FBI. The abuses have been extensive and well documented,” Wyden argued to colleagues. Wyden’s effort to strike the language failed by a vote of 34 to 58.
“Egregious Fourth Amendment violations against U.S. citizens will increase dramatically if this bill is passed into law,” Utah Republican Senator Mike Lee warned. Senator Rand Paul (R-KY) offered an amendment to block DHS, FBI, DOJ, IRS, and various ancillary intelligence, law enforcement, national parks and government agencies from buying Americans’ electronic NSA data from third parties and federal contractors. Paul’s amendment failed by a vote of 31 to 61.
The House and Senate bill does include provisions that would force the Intelligence Community to notify political leadership in Congress about 702 database searches involving lawmakers, but you, Comrade Citizen, are not allowed to know about the searches done on you. You, comrade prole, must improve your elite status if you wish to participate in any benefit from the shredded and reconfigured 4th Amendment, now reserved for the entitled class.
As noted by The Hill, Senator Mike “Lee offered an amendment to require the Foreign Intelligence Surveillance Court to appoint an outside lawyer to argue for the rights of a U.S. person the government wants to surveil secretly. It would have also required government employees appearing before the FISA court to disclose factual evidence that might call into question the accuracy of their statements. It also failed even though it had previously passed the Senate with 77 votes in 2020.”
Go figure!
Hey, stop me when you start to notice something that looks like history rhyming.
There’s an inversion afoot.
People in DC claim they cannot see it….
People in DC claim they don’t see the parallels…
People in DC hate my pesky annoyances….
People in DC are our abusers….
Throw sand into the machine whenever possible…
Wolverines!
165 Democrats voted for a foreign aid package brought to the floor by Republican Speaker Mike Johnson. The measure includes $26 billion more for Israel, $61 billion more for Ukraine and around $10 billion for Taiwan. 151 Republicans voted to support the aid bill.
There is almost $100 billion in total foreign aid and approximately $0 to secure the southern U.S. border. This is a “Republican” bill, that passed with Democrats, not Republicans. The ideological UniParty is very real in Washington DC, and this vote was entirely against the wishes of most Americans.
We are in an abusive relationship with our government. There really is no other way to look at it.
WASHINGTON DC – […] underscoring deep intraparty frustrations with Johnson’s strategy, 55 Republicans voted against advancing the package — a once unheard-of GOP rebellion that has grown more common given their single-digit margin.
Normally that would be enough to scuttle Johnson’s plan, but 165 Democrats voted to bring up the bills. It’s the first time they’ve done so during Johnson’s speakership — an alliance that is likely to fuel calls from his most vocal critics to strip him of his gavel.
The House is now slated to vote on the bills early Saturday afternoon, and Johnson will once again need substantial help from Democrats to get them over to the Senate. Majority Leader Steve Scalise said Friday that he plans to support the package, while Majority Whip Tom Emmer (R-Minn.) declined to state his position when asked.
“I’m pleased that we were able to come to a bipartisan agreement,” said House Appropriations Chair Tom Cole (R-Okla.). He added: “It’s working out the way the speaker wanted it to, which is that every member is free to vote their conscience … in a way they usually aren’t.”
The House structured the package so as to ease its consideration in the Senate, requiring less time and procedural votes to pass the upper chamber. While senators are scheduled to be out of Washington next week, there’s ongoing discussion about canceling that recess to take up the House plan if it passes. (read more)
It’s really not just Mike Johnson, the root of the issue is much deeper than just corrupt and detached Republican leadership. The issue extends to every aspect of life and politics in Washington DC. Every member is participating in a process to give money to other countries, regardless of whether the American voter wants that to happen or not.
There is a complete collapse of the governmental structure of the United States as it pertains to representative government. The concept of representative government is completely gone, not even considered any longer amid the professional political class from both wings of the UniParty vulture.
I have no idea how this structural collapse can be fixed. There doesn’t seem to be any entity willing to stop the nonsense as it relates to financial systems and U.S. foreign aid.
At a certain point amid all of this madness, you just have to elevate and accept the dollar-based U.S. Central Bank Digital Currency (USCBDC) is going to happen…. in large part because UniParty spending like this makes central bank digital currency a self-fulfilling prophecy.
Too few people understand how that USCBDC issue will fundamentally change the dynamic of everything…
The year 2015 was not long ago, and yet the entire world economy has changed. Central banks mismanaged monetary policy through arbitrarily low interest rates and continuous printing to appease the bigger issue—fiscal policy. Fiscal policies are all but nonexistent in most of the modern world, and government spending has become one of the largest threats to the global economy. The COVID lockdown pushed these issues into overdrive, and world leaders usurped power that they have refused to relinquish.
This is a global issue. Canada’s opposition leader Pierre Poilievre has highlighted how much has changed within one ECM cycle, as the last major turning point hit in 2015, and asked Parliament to imagine they had awoken from an 8-year coma.
Eight short years ago, Canada boasted one of the strongest middle classes in the modern world, surpassing that of America. Taxes were actually declining in Canada, falling faster than at any other time in the nation’s history. Crime had decreased by -25%, and people felt safe in their hometowns. The immigration system was efficient, the borders were closed, and there was no migrant crisis. Housing was affordable, costing less than half of what it does today. The nation had a balanced budget.
Poilievre mentioned that there were global conflicts at the time in Syria, Afghanistan, and even Ukraine but none of them were causing inflation at home. Prime Minister Harper had much different policies in place.
Inflation is now rampant, and even after hitting a 40-year high in 2023, it remains 50% above the 2% central bank target. Canada’s economy is shrinking per capita and is expected to have the worst OECD growth of all 40 member countries for the next five years. There is a massive housing crisis in Canada, surpassing that of America, and homelessness is on the rise. The Canadian borders are open, migrants are encouraged to come to the nation despite the lack of housing, and millions of unvetted migrants are now within Canadian boundaries. Taxes are rapidly rising as Trudeau supports World Economic Forum initiatives like carbon taxes and reducing fossil fuels at the expense of the people. Canada has sent a fortune to Ukraine and continues recklessly spending on initiatives that in no way benefit Canadians.
Poilievre is on Trudeau’s tail. It is no wonder that nearly half of Canadians wish to elect a new leader in 2024 instead of 2025. Trudeau is losing his grip over the Canadian people who have become disgruntled with the unsustainable cost of living, rising crime, and increasingly tyrannical government.
It is incredible how much can change within one wave of the ECM. I can assure you that the world will be a very different place by the next one.
Barack Obama and Eric Holder did not create a weaponized DOJ and FBI; instead, what they did was take the preexisting system and retool it so the weapons only targeted one side of the political continuum. This point is where many people understandably get confused.

In the era shortly after 9/11, the DC national security apparatus was constructed to preserve continuity of government and simultaneously view all Americans as potential threats. The Department of Homeland Security (DHS) and the Office of the Director of National Intelligence (ODNI) were created specifically for this purpose.
What Barack Obama and Eric Holder did with that new construct was refine the internal targeting mechanisms so that only their ideological opposition became the target of the new national security system. This is very important to understand as you dig deeper into this research outline.
Washington DC created the modern national security apparatus immediately and hurriedly after 9/11/01. DHS came along in 2002, and within the Intelligence Reform and Terrorism Prevention Act of 2004 the ODNI was formed. When Barack Obama and Eric Holder arrived a few years later, those newly formed institutions were viewed as opportunities to create a very specific national security apparatus that would focus almost exclusively against their political opposition.
The preexisting Federal Bureau of Investigation (FBI) and Dept of Justice (DOJ) were then repurposed to become two of the four pillars of the domestic national security apparatus. However, this new construct would have a targeting mechanism based on political ideology. The DHS, ODNI, DOJ and FBI became the four pillars of this new institution. Atop these pillars is where you will find the Fourth Branch of Government.
We were not sleeping when this happened, we were wide awake. However, we were stunningly distracted by the economic collapse that was taking place in 2006 and 2007 when the engineers behind Obama started to assemble the design. By the time Obama took office in 2009, we sensed something profound was shifting, but we can only see exactly what shifted in the aftermath. The four pillars were put into place, and a new Fourth Branch of Government was quietly created.
As time passed, and the system operators became familiar with their new tools, technology allowed the tentacles of the system to reach out and touch us. That is when we first started to notice that something very disconcerting was happening. Those four pillars are the root of it, and if we take the time to understand how the Fourth Branch originated, questions about this current state of perpetual angst will start to make sense.
Grab a cup of your favorite beverage, and take a walk with me as we outline how this was put together. You might find many of the questions about our current state of political affairs beginning to make a lot more sense.

Remember, it is not my intent to outline the entire history of how we got to this place where the intelligence community now acts as the superseding fourth branch of government. Such an effort would be exhausting and likely take our discussion away from understanding the current dynamic.
History provided enough warnings from Dwight D. Eisenhower (military), to John F. Kennedy (CIA), to Richard Nixon (FBI), to all modern versions of warnings and frustrations from HPSCI Devin Nunes and ODNI Ric Grenell. None of those prior reference points are invalid, and all documented outlines of historic reference are likely true and accurate. However, a generational review is not useful, as the reference impacting us ‘right now‘ gets lost.
Instead, we pick up the expansive and weaponized intelligence system as it manifests after 9/11/01, and my goal is to highlight how the modern version of the total intelligence apparatus has now metastasized into a Fourth Branch of Government. It is this superseding branch that now touches and influences every facet of our life.
If we take the modern construct, originating at the speed of technological change, we can also see how the oversight or “check/balance” in our system of government became functionally obsolescent.
After many years of granular research about the intelligence apparatus inside our government, in the summer of 2020 I visited Washington DC to ask specific questions. My goal was to go where the influence agents within government actually operate, and to discover the people deep inside the institutions no one elected and few people pay attention to.

It was during this process when I discovered how information is purposefully put into containment silos; essentially a formal process to block the flow of information between agencies and between the original branches. While frustrating to discover, the silo effect was important because understanding the communication between networks leads to our ability to reconcile conflict between what we perceive and what’s actually taking place.
After days of research and meetings in DC during 2020; amid a town that was serendipitously shut down due to COVID-19; I found a letter slid under the door of my room in a nearly empty hotel with an introduction of sorts. The subsequent discussions were perhaps the most important. After many hours of specific questions and answers on specific examples, I realized why our nation is in this mess. That is when I discovered the fourth and superseding branch of government, the Intelligence Branch.
I am going to explain how the Intelligence Branch works: (1) to control every other branch of government; (2) how it functions as an entirely independent branch of government with no oversight; (3) how and why it was created to be independent from oversight; (4) what is the current mission of the IC Branch, and most importantly (5) who operates it.
The Intelligence Branch is an independent functioning branch of government, it is no longer a subsidiary set of agencies within the Executive Branch as most would think. To understand the Intelligence Branch, we need to drop the elementary school civics class lessons about three coequal branches of government and replace that outlook with the modern system that created itself.
The Intelligence Branch functions much like the State Dept, through a unique set of public-private partnerships that support it. Big Tech industry collaboration with intelligence operatives is part of that functioning; almost like an NGO. However, the process is much more important than most think. In this problematic perspective of a corrupt system of government, the process is the flaw – not the outcome.
There are people making decisions inside this little known, unregulated and out-of-control branch of government that impact every facet of our lives.
None of the people operating deep inside the Intelligence Branch were elected, and our elected representative House members genuinely do not know how the system works. I assert this position affirmatively because I have talked to House and Senate staffers, including the chiefs of staff for multiple House & Senate committee seats. They are not malicious people; however, they are genuinely clueless of things that happen outside their silo. That is part of the purpose of me explaining it, with examples, in full detail with sunlight.
In April of 2016, the FBI launched a counterintelligence operation against presidential candidate Donald Trump. The questioning about that operation is what New York Representative Elise Stefanik cites in March of 2017, approximately 11 months later (First Two Minutes).
♦ Notice how FBI Director James Comey just matter-of-factly explains no one outside the DOJ was informed about the FBI operation. Why? Because that’s just the way things are done. His justification for unilateral operations was “because of the sensitivity of the matter“, totally ignoring any constitutional or regulatory framework for oversight; because, well, quite simply, there isn’t any. The intelligence apparatus inside the DOJ/FBI can, and does, operate based on their own independent determinations of authority.
♦ Notice also how FBI Director Comey shares his perspective that informing the National Security Council (NSC) is the equivalent of notifying the White House. The FBI leadership expressly believe they bear no responsibility to brief the Chief Executive. As long as they tell some unknown, unelected, bureaucratic entity inside the NSC, their unwritten responsibility to inform the top of their institutional silo is complete. If the IC wants to carve out the Oval Office, they simply plant information inside the NSC and, from their perspective, their civic responsibility to follow checks-and-balances is complete. This is an intentional construct.
♦ Notice how Comey obfuscates notification to the Director of National Intelligence (DNI), by avoiding the fact James Clapper was the DNI from outset of the counterintelligence operation throughout the remainder of Obama’s term. When I get deeper into the process, we will understand how the Intelligence Branch has intentionally used the creation of the DNI position (established post 9/11/01) as a method to avoid oversight, not enhance it. Keeping an oblivious doofus like James Clapper in position held strategic value [Doofus Reminder HERE].
That video of James Comey being questioned by Elise Stefanik was the first example given to me by someone who knew the background of everything that was taking place preceding that March 20, 2017, hearing. That FBI reference point is a key to understand how the Intelligence Branch operates with unilateral authority above Congress (legislative branch), above the White House (executive branch), and even above the court system (judicial branch).
Also, watch this short video of James Clapper because it is likely many readers have forgotten, and likely even more readers have never seen it. Watch closely how then White House national security adviser John Brennan is responding in that video. This is before Brennan became CIA Director, this is when Brennan was helping Barack Obama put the pillars into place. WATCH:
[Sidebar: Every time I post this video it gets scrubbed from YouTube (example), so save it if you ever want to see it again.]
The video of James Clapper highlights how the ODNI position (created with good national security intention) ended up becoming the fulcrum for modern weaponization, and is now an office manipulated by agencies with a vested interest in retaining power. The Intelligence Branch holds power over the ODNI through their influence and partnership with the body that authorizes the power within it, the Senate Select Committee on Intelligence (SSCI).
Factually, the modern intelligence apparatus uses checks and balances in their favor. The checks create silos of proprietary information, classified information, vaults of information that work around oversight issues. The silos are part of the problem.
Ironically, the Office of the Director of National Intelligence was created in the aftermath of 9/11/01 expressly to eliminate the silos of information which they felt led to a domestic terrorist attack that could have been prevented. The ODNI was created specifically upon the recommendation of the 9/11 commission.
The intent was to create a central hub of intelligence information, inside the Executive Branch, where the CIA, NSA, DoD, DoS, and DIA could deposit their unique intelligence products and a repository would be created so that domestic intelligence operations, like the DOJ and FBI could access them when needed to analyze threats to the U.S. This, they hoped, would ensure the obvious flags missed in the 9/11 attacks would not be missed again.
The DNI office created a problem for those who operate in the shadows of proprietary information. You’ll see how it was critical to install a person uniquely skilled in being an idiot, James Clapper, into that willfully blind role while intelligence operatives worked around the office to assemble the Intelligence Branch of Government.
• The last federal budget that flowed through the traditional budgetary process was signed into law in September of 2007 for fiscal year 2008 by George W. Bush. Every budget since then has been a fragmented process of continuing resolutions and individual spending bills.
Why does this matter? Because many people think defunding the Intelligence Community is a solution; it is not…. at least, not yet. Worse yet, the corrupt divisions deep inside the U.S. intelligence system can now fund themselves from multinational private sector partnerships (banks, corporations and foreign entities).
• When Democrats took over the House of Representatives in January 2007, they took office with a plan. Nancy Pelosi became Speaker, and Democrats controlled the Senate where Harry Reid was Majority Leader. Barack Obama was a junior senator from Illinois.
Pelosi and Reid intentionally did not advance a budget in 2008 (for fiscal year 2009) because their plan included installing Barack Obama (and all that came with him) with an open checkbook made even more lucrative by a worsening financial crisis and a process called baseline budgeting. Baseline budgeting means the prior fiscal year budget is accepted as the starting point for the next year budget. All previous expenditures are baked into the cake within baseline budgeting.
Massive bailouts preceded Obama’s installation due to U.S. economic collapse, and massive bailouts continued after his installation. This is the ‘never let a crisis go to waste’ aspect. TARP (Troubled Asset Recovery Program), auto bailouts (GM), and the massive stimulus spending bill, the American Recovery and Reinvestment Act (ARRA, ie. those shovel ready jobs) were all part of the non budget spending. The federal reserve assisted with Quantitative Easing (QE1 and QE2) as congress passed various Porkulous spending bills further spending and replacing the formal budget process.
Note: There has never been a budget passed in the normal/traditional process since September of 2007.
• While Obama’s radical ‘transformation‘ was triggered across a broad range of government institutions, simultaneously spending on the U.S. military was cut, but spending on the intelligence apparatus expanded. We were all distracted by Obamacare, and the Republican party wanted to keep us that way. However, in the background there was a process of transformation taking place that included very specific action by Eric Holder and targeted effort toward the newest executive agency the ODNI.

The people behind Obama, those same people now behind Joe Biden, knew from years of strategic planning that ‘radical transformation’ would require control over specific elements inside the U.S. government. Eric Holder played a key role in his position as U.S. Attorney General in the DOJ.
AG Holder recruited ideologically aligned political operatives who were aware of the larger institutional objectives. One of those objectives was weaponizing the DOJ-National Security Division (DOJ-NSD) a division inside the DOJ that had no inspector general oversight. For most people the DOJ-NSD weaponization surfaced with a hindsight awakening of the DOJ-NSD targeting candidate Donald Trump many years later. However, by then the Holder crew had executed almost eight full years of background work.
• The second larger Obama/Holder objective was control over the FBI. Why was that important? Because the FBI does the domestic investigative work on anyone who needs or holds a security clearance. The removal of security clearances could be used as a filter to further build the internal ideological army they were assembling. Additionally, with new power in the ODNI created as a downstream consequence of the Patriot Act, new protocols for U.S. security clearances were easy to justify.
Carefully selecting fellow ideological travelers was facilitated by this filtration within the security clearance process. How does that issue later manifest? Just look around at how politicized every intelligence agency has become, specifically including the FBI.
• At the exact same time this new background security clearance process was ongoing, again everyone distracted by the fight over Obamacare, inside the Department of State (Secretary Hillary Clinton) a political alignment making room for the next phase was being assembled. Names like Samantha Power, Susan Rice and Hillary Clinton were familiar on television while Lisa Monaco worked as a legal liaison between the Obama White House and Clinton State Department.
Through the Dept of State (DoS) the intelligence apparatus began working on their first steps to align Big Tech with a larger domestic institutional objective. Those of you who remember the “Arab Spring”, some say “Islamist Spring”, will remember it was triggered by Barack Obama’s speech in Cairo – his first foreign trip. The State Department worked with grassroots organizers (mostly Muslim Brotherhood) in Egypt, Syria, Bahrain, Qatar and Libya. Obama leaned heavily on the organizational network of Turkish President Recep Erdogan for contacts and support.
Why does this aspect matter to us? Well, you might remember how much effort the Obama administration put into recruiting Facebook and Twitter as resources for the various mideast rebellions the White House and DoS supported. This was the point of modern merge between the U.S. intelligence community and Big Tech social media.
In many ways, the coordinated political outcomes in Libya and Egypt were the beta test for the coordinated domestic political outcomes we saw in the 2020 U.S. presidential election. The U.S. intelligence community working with social media platforms and political operatives.
Overlaying all of that background activity was also a new alignment of the Obama-era intelligence apparatus with ideological federal “contractors“. Where does this contractor activity manifest? In the FISA Court opinion of Rosemary Collyer who cited the “interagency memorandum of understanding”, or MOU.
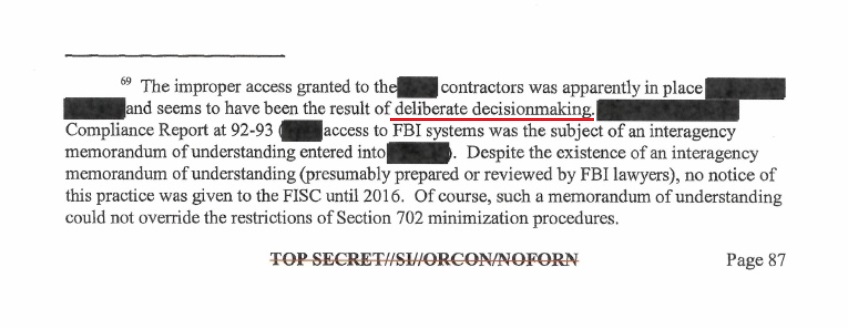
Hopefully, you can see a small part of how tentacled the system to organize/weaponize the intelligence apparatus was. None of this was accidental, all of this was by design, and the United States Senate was responsible for intentionally allowing most of this to take place.
That’s the 30,000/ft level backdrop history of what was happening as the modern IC was created. Next we will go into how all these various intelligence networks began working in unison and how they currently control all of the other DC institutions under them; including how they can carve out the President from knowing their activity.
♦ When Barack Obama was installed in January 2009, the Democrats held a 60 seat majority in the U.S. Senate. As the people behind the Obama installation began executing their longer-term plan, the Senate Select Committee on Intelligence was a tool to create the Intelligence Branch; it was not an unintentional series of events.
When Obama was installed, Dianne Feinstein was the Chair of the Senate Select Committee on Intelligence (SSCI), and Democrat operative Dan Jones was her lead staffer. Feinstein was completely controlled by those around her including Senate Majority Leader Harry Reid. The CIA was in the process of turning over personnel following the Bush era, and as a result of a massive multi-year narrative of diminished credibility (Iraq WMD), a deep purge was underway. Obama/Holder were in the process of shifting intelligence alignment and the intensely political Democrat Leader Harry Reid was a key participant.

THE TRAP – Many people say that Congress is the solution to eliminating the Fourth and superseding Branch of Government, the Intelligence Branch. This is an exercise in futility because the Legislative Branch, specifically the SSCI, facilitated the creation of the Intelligence Branch. The SSCI cannot put the genie they created back in the bottle without admitting they too are corrupt; and the background story of their corruption is way too intense to be exposed now.
Every member of the SSCI is compromised in some controlling manner. Those Senators who disliked the control over them; specifically disliked because the risk of sunlight was tenuous and, well, possible; have either left completely or stepped down from the committee. None of the SSCI members past or present would ever contemplate saying openly what their tenure involved.
[Note: You might remember when Vice Chairman Mark Warner’s text messages surfaced, there was a controlled Republican SSCI member who came to his defense in February of 2018. It was not accidental that exact Senator later became the chair of the SSCI himself. That Republican Senator is Marco Rubio, now vice-chair since the Senate re-flipped back to the optics of Democrat control in 2021.]
All of President Obama’s 2009 intelligence appointments required confirmation from the Senate. The nominees had to first pass through the Democrat controlled SSCI, and then to a full Senate vote where Democrats held a 60 vote majority. Essentially, Obama got everyone he wanted in place easily. Rahm Emmanuel was Obama’s Chief of Staff, and Valerie Jarrett was Senior Advisor.

Tim Geithner was Treasury Secretary in 2010 when the joint DOJ/FBI and IRS operation to target the Tea Party took place after the midterm “shellacking” caused by the Obamacare backlash. Mitch McConnell was Minority Leader in the Senate but supported the targeting of the Tea Party as his Senate colleagues were getting primaried by an angry and effective grassroots campaign. McConnell’s friend, Senator Bob Bennett, getting beaten in Utah was the final straw.
Dirty Harry and Mitch McConnell saw the TEA Party through the same prism. The TEA Party took Kennedy’s seat in Massachusetts (Scott Brown); Sharon Angle was about to take out Harry Reid in Nevada; Arlen Spector was taken down in Pennsylvania; Senator Robert Byrd died; Senator Lisa Murkowski lost her primary to Joe Miller in Alaska; McConnell’s nominee Mike Castle lost to Christine O’Donnell in Delaware; Rand Paul won in Kentucky. This is the background. The peasants were revolting…. and visibly angry Mitch McConnell desperately made a deal with the devil to protect himself.
In many ways, the TEA Party movement was/is very similar to the MAGA movement. The difference in 2010 was the absence of a head of the movement, in 2015 Donald Trump became that head figure who benefited from the TEA Party energy. Trump came into office in 2017 with the same congressional opposition as the successful TEA Party candidates in 2011.
Republicans took control of the Senate following the 2014 mid-terms. Republicans took control of the SSCI in January 2015. Senator Richard Burr became chairman of the SSCI, and Dianne Feinstein shifted to Vice-Chair. Dirty Harry Reid left the Senate, and Mitch McConnell took power again.
Republicans were in control of the Senate Intelligence Committee in 2015 when the Intelligence Branch operation against candidate Donald Trump was underway. [Feinstein’s staffer, Dan Jones, left the SSCI so he could act as a liaison and political operative between private-sector efforts (Fusion GPS, Chris Steele) and the SSCI.] The SSCI was a participant in that Fusion-GPS/Chris Steele operation, and as a direct consequence Republicans were inherently tied to the problem with President Trump taking office in January of 2017. Indiana Republican Senator Dan Coats was a member of the SSCI.
Bottom line…. When it came to the intelligence system targeting Donald Trump during the 2015/2016 primary, the GOP was just as much at risk as their Democrat counterparts.
When Trump unexpectedly won the 2016 election, the SSCI was shocked more than most. They knew countermeasures would need to be deployed to protect themselves from any exposure of their intelligence conduct. Dianne Feinstein stepped down, and Senator Mark Warner was elevated to Vice Chairman.
Indiana’s own Mike Pence, now Vice President, recommended fellow Hoosier, SSCI Senator Dan Coats, to become President Trump’s Director of National Intelligence (ODNI). [Apply hindsight here]
• To give an idea of the Intelligence Branch power dynamic, remind yourself how House Permanent Select Committee on Intelligence (HPSCI), Chairman Devin Nunes, tried to get access to the DOJ/FBI records of the FISA application used against the Trump campaign via Carter Page.
Remember, Devin Nunes only saw a portion of the FISA trail from his review of a Presidential Daily Brief (PDB) previously given to President Obama. Chairman Nunes had to review the PDB at the White House SCIF due to compartmented intelligence, another example of the silo benefit.
Remember the massive stonewalling and blocking of the DOJ/FBI toward Nunes? Remember the back and forth battle over declassification surrounding the Nunes memo?
Remember, after Nunes went directly to House Speaker Paul Ryan for help (didn’t get any), the DOJ only permitted two members from each party within the HPSCI to review the documents, and only at the DOJ offices of main justice?
Contrast that amount of House Intel Committee railroading and blocking by intelligence operatives in the DOJ, DOJ-NSD and FBI, with the simple request by Senate Intelligence Vice Chairman Mark Warner asking to see the Carter Page FISA application and immediately a copy being delivered to him on March 17th 2017.
Can you see which intelligence committee is aligned with the deepest part of the deep state?
Oh, how quickly we forget:
The contrast of ideological alignment between the House, Senate and Intelligence Branch is crystal clear when viewed through the prism of cooperation. You can see which legislative committee holds the power and support of the Intelligence Branch. The Senate Intel Committee facilitates the corrupt existence of the IC Branch, so the IC Branch only cooperates with the Senate Intel Committee. It really is that simple.
• The Intelligence Branch carefully selects its own members by controlling how security clearances are investigated and allowed (FBI). The Intelligence Branch also uses compartmentalization of intelligence as a way to keep each agency, and each downstream branch of government (executive, legislative and judicial), at arms length as a method to stop anyone from seeing the larger picture of their activity. I call this the “silo effect“, and it is done by design.
I have looked at stunned faces when I presented declassified silo product from one agency to the silo customers of another. You would be astonished at what they don’t know because it is not in their ‘silo’.

Through the advise and consent rules, the Intelligence Branch uses the SSCI to keep out people they consider dangerous to their ongoing operations. Any appointee to the intelligence community must first pass through the Senate Select Committee on Intelligence, before they get a full Senate vote. If the SSCI rejects the candidate, they simply refuse to take up the nomination. The president is then blocked from that appointment. This is what happened with President Trump over-and-over again.
• Additionally, the Intelligence Branch protects itself, and its facilitating allies through the formal classification process. The Intelligence Branch gets to decide unilaterally what information will be released and what information will be kept secret. There is no entity outside the Intelligence Branch, and yes that includes the President of the United States, who can supersede the classification authority of the Intelligence Branch. {Go Deep} and {Go Deep} This is something 99.9% of the people on our side get totally and frustratingly wrong.
No one can declassify, or make public, anything the Intelligence Branch will not agree to. Doubt this? Ask Ric Grenell, John Ratcliffe, or even President Trump himself.
• The classification process is determined inside the Intelligence Branch, all by themselves. They get to choose what rank of classification exists on any work-product they create; and they get to decide what the classification status is of any work product that is created by anyone else. The Intelligence Branch has full control over what is considered classified information and what is not. The Intelligence Branch defines what is a “national security interest” and what is not. A great technique for hiding fingerprints of corrupt and illegal activity.
[For familiar reference see the redactions to Lisa Page and Peter Strzok text messages. The Intelligence Branch does all redactions.]
• Similarly, the declassification process is a request by an agency, even a traditionally superior agency like the President of the United States, to the Intelligence Branch asking for them to release the information. The Intelligence Branch again holds full unilateral control. If the head of the CIA refuses to comply with the declassification instruction of the President, what can the president do except fire him/her? {Again, GO DEEP} How does the President replace the non-compliant cabinet member? They have to go through the SSCI confirmation. See the problem?
Yes, there are ways to break up the Intelligence Branch, but they do not start with any congressional effort. As you can see above, the process is the flaw – not the solution. Most conservative pundits have their emphasis on the wrong syllable. Their cornerstone is false.
For their own self-preservation, the Intelligence Branch has been interfering in our elections for years. The way to tear this apart begins with STATE LEVEL election reform that blocks the Legislative Branch from coordinating with the Intelligence Branch.
The extreme federalism approach is critical and also explains why Joe Biden has instructed Attorney General Merrick Garland to use the full power of the DOJ to stop state level election reform efforts. The worry of successful state level election control is also why the Intelligence Branch now needs to support the federal takeover of elections.
Our elections have been usurped by the Intelligence Branch. Start with honest elections and we will see just how much Democrat AND Republican corruption is dependent on manipulated election results. Start at the state level. Start there…. everything else is downstream.

♦ People want examples, reference points for work the Intelligence Branch conducts, specifically how it protects itself.
Yes, the history of the U.S. national security apparatus goes back decades; however, the weaponization of that apparatus, the creation of an apex branch of government, the Intelligence Branch, originated –as we currently feel it– under President Barack Obama.
Obama took the foundational tools created by Bill Clinton and George W. Bush and used the intelligence system architecture to create a weapon for use in his fundamental transformation. An alliance of ideologues within government (intel community) and the private sector (big tech and finance) was assembled, and the largest government weapon was created. Think about this every time you take your shoes off at an airport.
After the weapon was assembled and tested (Arab Spring), the Legislative Branch was enjoined under the auspices of a common enemy, Donald J. Trump, an outsider who was a risk to every entity in the institutional construct of Washington DC. Trillions were at stake, and years of affluence and influence were at risk as the unholy alliance was put together.
To understand the risk that Julian Assange represented to U.S. Intelligence Branch interests, it is important to understand just how extensive the operations of the FBI/CIA were in 2016.
It is within the network of foreign and domestic intel operations where Intelligence Branch political tool, FBI Agent Peter Strzok, was working as a bridge between the CIA and FBI counterintelligence operations.
By now, people are familiar with the construct of CIA operations involving Joseph Mifsud, the Maltese professor generally identified as a western intelligence operative who was tasked by the FBI/CIA to run an operation against Trump campaign official George Papadopoulos in both Italy (Rome) and London. {Go Deep}
In a similar fashion, the FBI tasked U.S. intelligence asset Stefan Halper to target another Trump campaign official, Carter Page. Under the auspices of being a Cambridge Professor, Stefan Halper also targeted General Michael Flynn. Additionally, using assistance from a female FBI agent under the false name Azra Turk, Halper also targeted Papadopoulos.
The initial operations to target Flynn, Papadopoulos and Page were all based overseas. This seemingly makes the CIA exploitation of the assets and the targets much easier.
HPSCI Ranking Member Devin Nunes outlined how very specific exculpatory evidence was known to the FBI and yet withheld from the FISA application used against Carter Page that also mentions George Papadopoulos. The FBI also fabricated information in the FISA.
However, there is an aspect to the domestic U.S. operation that also bears the fingerprints of the international intelligence apparatus; only this time, due to the restrictive laws on targets inside the U.S., the CIA aspect is less prominent. This is where FBI Agent Peter Strzok working for both agencies was important.
Remember, it’s clear in the text messages Strzok had a working relationship with what he called their “sister agency”, the CIA. Additionally, former CIA Director John Brennan has admitted Strzok helped write the January 2017 Intelligence Community Assessment (ICA) which outlines the Russia narrative; and Peter Strzok wrote the July 31st, 2016, “Electronic Communication” that originated FBI operation “Crossfire Hurricane.” Strzok immediately used that EC to travel to London to debrief allied intelligence officials connected to the Australian Ambassador to the U.K, Alexander Downer.
In short, Peter Strzok acted as a bridge between the CIA and the FBI. The perfect type of FBI career agent for the Intelligence Branch and CIA Director John Brennan to utilize.
Fusion GPS founder Glenn Simpson hired CIA Open Source analyst Nellie Ohr toward the end of 2015; at appropriately the same time as “FBI Contractors” were identified exploiting the NSA database and extracting information on a specific set of U.S. persons, the 2015 GOP candidates for President.
It was also Fusion GPS founder Glenn Simpson who was domestically tasked with a Russian lobbyist named Natalia Veselnitskaya. A little reported Russian Deputy Attorney General named Saak Albertovich Karapetyan was working double agents for the CIA and Kremlin. Karapetyan was directing the foreign operations of Natalia Veselnitskaya, and Glenn Simpson was organizing her inside the U.S.
Glenn Simpson managed Veselnitskaya through the 2016 Trump Tower meeting with Donald Trump Jr. However, once the CIA/Fusion-GPS operation using Veselnitskaya started to unravel with public reporting… back in Russia Deputy AG Karapetyan died in a helicopter crash.
Simultaneously timed in late 2015 through mid 2016, there was a domestic FBI operation using a young Russian named Maria Butina tasked to run up against republican presidential candidates. According to Patrick Byrne, Butina’s private sector handler [NOTE: remember, the public-private sector partnership], it was FBI agent Peter Strzok who was giving Patrick Byrne the instructions on where to send Butina. {Go Deep}
All of this context outlines the extent to which the FBI/CIA was openly involved in constructing a political operation that eventually settled upon anyone in candidate Donald Trump’s orbit. The international operations of the Intelligence Branch were directed by the FBI/CIA; and the domestic operations were coordinated by Peter Strzok operating with a foot in both agencies. [Strzok gets CIA service coin]
Recap: ♦Mifsud tasked against Papadopoulos (CIA). ♦Halper tasked against Flynn (CIA), Page (CIA), and Papadopoulos (CIA). ♦Azra Turk, pretending to be a Halper asst, tasked against Papadopoulos (FBI). ♦Veselnitskaya tasked against Donald Trump Jr (CIA, Fusion-GPS). ♦Butina tasked against Donald Trump Jr (FBI). All of these activities were coordinated.
Additionally, Christopher Steele was a British intelligence officer, hired by Fusion GPS to assemble and launder fraudulent intelligence information within his dossier. And we cannot forget Oleg Deripaska, a Russian oligarch, who was recruited by Asst. FBI Director Andrew McCabe to participate in running an operation against the Trump campaign and create the impression of Russian involvement. However, Deripaska refused to participate.
All of this foreign and domestic engagement was directly controlled by collaborating U.S. intelligence agencies from inside the Intelligence Branch. And all of this coordinated activity was intended to give a specific Russia influence/interference impression.
♦ The key point of all that background context is to see how committed the Intelligence Branch was to the constructed narrative of Russia interfering with the 2016 election. The CIA, FBI, and by extension the DOJ and DOJ-NSD, put a hell of a lot of work into it.
We also know that John Durham looked at the construct of the Intelligence Community Assessment (ICA); and talked to CIA analysts who participated in the construct of the January 2017 report that bolstered the false appearance of Russian interference in the 2016 election. This is important because it ties in to the next part that involves Julian Assange and Wikileaks.
On April 11th, 2019, the Julian Assange indictment was unsealed in the EDVA. From the indictment we discover it was under seal since March 6th, 2018:
On Tuesday April 15th more investigative material was released. Again, note the dates: Grand Jury, *December of 2017* This means FBI investigation prior to….
The FBI investigation took place prior to December 2017, and it was coordinated through the Eastern District of Virginia (EDVA) where Dana Boente was U.S. Attorney at the time. The grand jury indictment was sealed from March of 2018 until after Mueller completed his investigation, April 2019.
Why the delay?
What was the DOJ waiting for?
Here’s where it gets interesting….
The FBI submission to the Grand Jury in December of 2017 was four months after Congressman Dana Rohrabacher talked to Julian Assange in August of 2017: “Assange told a U.S. congressman … he can prove the leaked Democratic Party documents … did not come from Russia.”
(August 2017, The Hill Via John Solomon) Julian Assange told a U.S. congressman on Tuesday he can prove the leaked Democratic Party documents he published during last year’s election did not come from Russia and promised additional helpful information about the leaks in the near future.
Rep. Dana Rohrabacher, a California Republican who is friendly to Russia and chairs an important House subcommittee on Eurasia policy, became the first American congressman to meet with Assange during a three-hour private gathering at the Ecuadorian Embassy in London, where the WikiLeaks founder has been holed up for years.
Rohrabacher recounted his conversation with Assange to The Hill.
“Our three-hour meeting covered a wide array of issues, including the WikiLeaks exposure of the DNC [Democratic National Committee] emails during last year’s presidential election,” Rohrabacher said, “Julian emphatically stated that the Russians were not involved in the hacking or disclosure of those emails.”
Pressed for more detail on the source of the documents, Rohrabacher said he had information to share privately with President Trump. (read more)
Knowing how much effort the Intelligence Branch put into the false Russia collusion-conspiracy narrative, it would make sense for the FBI to take keen interest after this August 2017 meeting between Rohrabacher and Assange, monitor all activity, and why the FBI would quickly gather specific evidence (related to Wikileaks and Bradley Manning) for a grand jury by December 2017.
Within three months of the EDVA grand jury, the DOJ generated an indictment and sealed it in March 2018.
The DOJ sat on the indictment while the Mueller/Weissmann probe was ongoing.
As soon as the Mueller/Weissmann probe ended, on April 11th, 2019, a planned and coordinated effort between the U.K. and U.S. was executed; Julian Assange was forcibly arrested and removed from the Ecuadorian embassy in London, and the EDVA indictment was unsealed (link).
As a person who has researched this fiasco; including the ridiculously false 2016 Russian hacking/interference narrative: “17 intelligence agencies”, Joint Analysis Report (JAR) needed for Obama’s anti-Russia narrative in December ’16; and then a month later the ridiculously political Intelligence Community Assessment (ICA) in January ’17; this timing against Assange is too coincidental.
It doesn’t take a deep researcher to see the aligned Deep State motive to control Julian Assange. The Weissmann/Mueller report was dependent on Russia cybercrimes for justification, and that narrative was contingent on the Russia DNC hack story which Julian Assange disputes.
♦ This is critical. The Weissmann/Mueller report contains claims that Russia hacked the DNC servers as the central element to the Russia interference narrative in the U.S. election. This claim is directly disputed by WikiLeaks and Julian Assange, as outlined during the Dana Rohrabacher interview, and by Julian Assange on-the-record statements.
The predicate for Robert Mueller’s investigation was specifically due to Russian interference in the 2016 election.
The fulcrum for this Russia interference claim is the intelligence community assessment; and the only factual evidence claimed within the ICA is that Russia hacked the DNC servers; a claim only made possible by relying on forensic computer analysis from Crowdstrike, a DNC and FBI contractor.
The CIA holds a self-interest in upholding the Russian hacking claim; the FBI holds an interest in maintaining that claim; the U.S. media hold an interest in maintaining that claim. All of the foreign countries whose intelligence apparatus participated with Brennan and Strzok also have a self-interest in maintaining that Russia hacking and interference narrative.

Julian Assange is the only person with direct knowledge of how Wikileaks gained custody of the DNC emails; and Assange has claimed he has evidence it was not from a hack.
This “Russian hacking” claim was ultimately important to the CIA, FBI, DOJ, ODNI and U.K intelligence apparatus, it forms the corner of their justification. With that level of importance, well, right there is the obvious motive to shut Julian Assange down as soon as intelligence officials knew the Weissmann/Mueller report was going to be public.
…. and that’s exactly what they did. They threw a bag over Assange.
♦ COLLAPSED OVERSIGHT – The modern system to ‘check’ the Executive Branch was the creation of the legislative “Gang of Eight,” a legislative oversight mechanism intended to provide a bridge of oversight between the authority of the intelligence community within the Executive Branch.
The Go8 construct was designed to allow the President authority to carry out intelligence operations and provide the most sensitive notifications to a select group within Congress.
The Go8 oversight is directed to the position, not the person, and consists of: (1) The Speaker of the House; (2) The Minority Leader of the House; (3) The Chair of the House Permanent Select Committee on Intelligence, HPSCI; (4) The Ranking Member (minority) of the HPSCI; (5) The Leader of the Senate; (6) The Minority Leader of the Senate; (7) The Chair of the Senate Select Committee on Intelligence, SSCI; and finally (8) the Vice-Chair of the SSCI.
Example: When the Chief Executive (the President) initiates an intelligence operation on behalf of the United States, the President triggers a “finding memo.” In essence, the instruction to the intel agency or agencies to authorize a covert operation. When that process takes place, the Go8 are the first people notified. Depending on the sensitivity of the operation, sometimes the G08 are notified immediately after the operation is conducted. The notification can be a phone call or an in-person briefing.
Because of the sensitivity of their intelligence information, the Gang of Eight hold security clearances that permit them to receive and review all intelligence operations. The intelligence community are also responsible for briefing the Go8 with the same information they use to brief the President.

The Go8 design is intended to put intelligence oversight upon both political parties in Congress; it is designed that way by informing the minority leaders of both the House and Senate as well as the ranking minority members of the SSCI and HPSCI. Under the concept, the President cannot conduct an intelligence operation; and the intelligence community cannot carry out intelligence gathering operations without the majority and minority parties knowing about it.
The modern design of this oversight system was done to keep rogue and/or corrupt intelligence operations from happening. However, as we shared in the preview to this entire discussion, the process was usurped during the Obama era. {GO DEEP}
Former FBI Director James Comey openly admitted to Congress on March 20, 2017, that the FBI, FBI Counterintelligence Division, DOJ and DOJ-National Security Division, together with the Office of the Director of National Intelligence (ODNI) and the CIA, had been conducting independent investigations of Donald Trump for over a year without informing the Go8. Comey justified the lack of informing Go8 oversight by saying, “because of the sensitivity of the matter.”
Stupidly, Congress never pressed James Comey on that issue. The arrogance was astounding, and the acceptance by Congress was infuriating. However, that specific example highlighted just how politically corrupt the system had become. In essence, Team Obama usurped the entire design of congressional oversight…. and Congress just brushed it off.
Keep in mind, Comey did not say the White House was unaware; in fact he said exactly the opposite, he said, “The White House was informed through the National Security Council,” (the NSC). The implication, the very direct and specific implication; the unavoidable implication and James Comey admission that everyone just brushed aside, was that President Obama’s National Security Advisor, Susan Rice, was totally informed of the intelligence operation(s) against Donald Trump. After all, the NSC reports to the National Security Advisor.
Does the January 20, 2017, Susan Rice memo look different now?
Again, no one saw the immediate issue. What Comey just described on that March day in 2017 was the total usurpation of the entire reason the Gang of Eight exists; to eliminate the potential for political weaponization of the Intelligence Community by the executive branch. The G08 notifications to the majority and minority are specifically designed to make sure what James Comey admitted to doing was never supposed to happen.
Team Obama carried out a political operation using the intelligence community and the checks-and-balances in the system were intentionally usurped. This is an indisputable fact.
Worse still, the entire legislative branch of Congress, which specifically includes the Republicans that now controlled the House and Senate, did nothing. They just ignored what was admitted. The usurpation was willfully ignored. The mechanism of the G08 was bypassed without a twitch of condemnation or investigation…. because the common enemy was Donald Trump.
This example highlights the collapse of the system. Obama, the executive branch, collapsed the system by usurping the process; in essence the process became the bigger issue and the lack of immediate legislative branch reaction became evidence of open acceptance. The outcomes of the usurpation played out over the next four years, Donald J. Trump was kneecapped and lost his presidency because of it. However, the bigger issue of the collapse still exists.
The downstream consequence of the Legislative Branch accepting the Executive Branch usurpation meant both intelligence committees were compromised. Additionally, the leadership of both the House and Senate were complicit. Think about this carefully. The Legislative Branch allowance of the intelligence usurpation meant the Legislative Branch was now subservient to the Intelligence Branch.
That’s where we are.
Right now.
That’s where we are.
Term-3 Obama is now back in the White House with Joe Biden.
Term-1 and Term-2 Obama usurped the ‘check and balance‘ within the system and weaponized the intelligence apparatus. During Trump’s term that weaponization was covered up by a compliant congress, and not a single member of the oversight called it out. Now, Term-3 Obama steps back in to continue the cover up and continue the weaponization.
Hopefully, you can now see the scale of the problem that surrounds us with specific citation for what has taken place. What I just explained to you above is not conspiracy theory, it is admitted fact that anyone can look upon. Yet….
Have you seen this mentioned anywhere? Have you seen this called out by anyone in Congress? Have you seen anyone in media (ally or adversary) call this out? Have you seen any member of the Judicial Branch stand up and say wait, what is taking place is not okay? Have you seen a single candidate for elected office point this out? Have you seen anyone advising a candidate point this out?
This is our current status. It is not deniable. The truth exists regardless of our comfort.
Not a single person in power will say openly what has taken place. They are scared of the Fourth Branch. The evidence of what has taken place is right there in front of our face. The words, actions and activities of those who participated in this process are not deniable.
There are only two members of the Gang of Eight who have existed in place from January 2007 (the real beginning of Obama’s term, two years before he took office when the Congress flipped). Only two members of the G08 have been consistently in place from January of 2007 to right now, today. All the others came and went, but two members of the Gang of Eight have been part of that failed and collapsed oversight throughout the past 15 years, Nancy Pelosi and Mitch McConnell.

♦ TECHNOLOGY – On a global scale – the modern intelligence gathering networks are now dependent on data collection to execute their intelligence missions. In the digital age nations have been executing various methods to gather that data. Digital surveillance has replaced other methods of interception. Those surveillance efforts have resulted in a coalescing of regional data networks based on historic multi-national relationships.
We have a recent frame of reference for the “U.S. data collection network” within the NSA. Through the allied process the Five Eyes nations all rely on the NSA surveillance database (U.K, Australia, Canada, New Zealand and U.S.) The NSA database provides the digital baseline for intelligence operations in defense of our allies. The portals into the NSA database are essentially an assembly of allies in like-minded ideological connection to the United States.
Unfortunately, there have been some revelations about the NSA database being used to monitor our allies, like in the example of Germany and surveillance on Angela Merkel’s phone. As long as “the good guys” are operating honorably, allies of the United States can feel confident about having protection from the NSA surveillance of global digital data. We warn our friends if we detect something dangerous etc.
The U.S. has nodes on communication pipelines to intercept and extract data. We have also launched hundreds, perhaps thousands, of satellites to conduct surveillance and gather up data. All of this data is fed into the NSA database where it is monitored (presumably) as a national security mechanism, and in defense of our allies.
However, what about data collection or data networks that are outside the NSA database? What do our enemies do? The NSA database is just one intelligence operation of digital surveillance amid the entire world, and we do not allow access by adversaries we are monitoring. So what do they do? What do our allies do who might not trust the United States due to past inconsistencies, ie. the Middle East?
The answers to those questions highlight other data collection networks. So a brief review of the major players is needed.
♦ CHINA – China operates their own database. They, like the NSA, scoop up data for their system. Like us, China launches satellites and deploys other electronic data collection methods to download into their database. This is why the issues of electronic devices manufactured in China becomes problematic. Part of the Chinese data collection system involves the use of spyware, hacking and extraction.
Issues with Chinese communication company Huawei take on an added dimension when you consider the goal of the Chinese government to conduct surveillance and assemble a network of data to compete with the United States via the NSA. Other Chinese methods of surveillance and data-collection are less subversive, as in the examples of TicTok and WeChat. These are Chinese social media companies that are scraping data just like the NSA scrapes data from Facebook, Twitter and other Silicon Valley tech companies. [ Remember, the Intelligence Branch is a public-private partnership. ]
♦ RUSSIA – It is very likely that Russia operates their own database. We know Russia launches satellites, just like China and the USA, for the same purposes. Russia is also very proficient at hacking into other databases and extracting information to store and utilize in their own network. The difference between the U.S., China and Russia is likely that Russia spends more time on the hacking aspect because they do not generate actual technology systems as rapidly as the U.S. and China.
The most recent database creation is an outcome of an ally having to take action because they cannot rely on the ideology of the United States remaining consistent, as the administrations ping-pong based on ideology.
♦ SAUDI ARABIA – Yes, in 2016 we discovered that Saudi Arabia was now operating their own intelligence data-gathering operation. It would make sense, given the nature of the Middle East and the constant fluctuations in political support from the United States. It is a lesson the allied Arab community and Gulf Cooperation Council learned quickly when President Obama went to Cairo in 2009 and launched the Islamist Spring (Arab Spring) upon them.


I have no doubt the creation of the Saudi intelligence network was specifically because the Obama administration started supporting radical Islamists within the Muslim Brotherhood, and threw fuel on the fires of extremism all over the Arab world.
Think about it., What would you do if you were Saudi Arabia, Egypt, Bahrain, Kuwait, the UAE, Jordan, Oman or Yemen and you knew the United States could just trigger an internal uprising of al-Qaeda, ISIS and the political arm of the Muslim Brotherhood to seek your destruction?
Without a doubt, those urgent lessons from 2009, 2010, 2011 triggered the formation of the Arab Intelligence Network as a network to defend itself with consistency. They assembled the network and activated it in 2017 as pictured above.
♦ Israel – Along a similar outlook to the Arab network, no doubt Israel operates an independent data collection system as a method of protecting itself from ever-changing U.S. politics amid a region that is extremely hostile to its very existence. Like the others, Israel launches proprietary satellites, and we can be sure they use covert methods to gather electronic data just like the U.S. and China.
As we have recently seen in the Pegasus story, Israel creates spyware programs that are able to track and monitor cell phone communications of targets. The spyware would not work unless Israel had access to some network where the phone meta-data was actually stored. So yeah, it makes sense for Israel to operate an independent intelligence database.
♦ Summary: As we understand the United States Intelligence Branch of government as the superseding entity that controls the internal politics of our nation, we also must consider that multiple nations have the same issue. There are major intelligence networks around the world beside the NSA “Five-Eyes” database. China, Russia, Saudi Arabia and Israel all operate proprietary databases deploying the same tools and techniques for assembly.
The geopolitical conflict that has always existed has now shifted into a digital battle-space. The Intelligence Agencies from these regions are now operating as the backbone of the government that uses them, and has become dependent on them. [<- Reread that].
Once you accept the digital-era intelligence apparatus of China, Russia, Saudi-Arabia, The United States and Israel, are now the primary national security mechanisms for stabilization of government; then you accept the importance of those intelligence operations.
Once you understand how foundational those modern intelligence operations have become for the stability and continuity of those governments…… then you begin to understand just how the United States intelligence community became more important than the government that created it.
♦ Public Private Partnership – The modern Fourth Branch of Government is only possible because of a Public-Private partnership with the intelligence apparatus. You do not have to take my word for it, the partnership is so brazen they have made public admissions.

The biggest names in Big Tech announced in June their partnership with the Five Eyes intelligence network, ultimately controlled by the NSA, to: (1) monitor all activity in their platforms; (2) identify extremist content; (3) look for expressions of Domestic Violent Extremism (DVE); and then, (4) put the content details into a database where the Five Eyes intelligence agencies (U.K., U.S., Australia, Canada, New Zealand) can access it.
Facebook, Twitter, Google and Microsoft are all partnering with the intelligence apparatus. It might be difficult to fathom how openly they admit this, but they do. Look at this sentence in the press release (emphasis mine):
[…] “The Group will use lists from intelligence-sharing group Five Eyes adding URLs and PDFs from more groups, including the Proud Boys, the Three Percenters and neo-Nazis.”
Think about that sentence structure very carefully. They are “adding to” the preexisting list…. admitting the group (aka Big Tech) already have access to the the intelligence-sharing database… and also admitting there is a preexisting list created by the Five Eyes consortium.
Obviously, who and what is defined as “extremist content” will be determined by the Big Tech insiders themselves. This provides a gateway, another plausible deniability aspect, to cover the Intelligence Branch from any oversight.
When the Intelligence Branch within government wants to conduct surveillance and monitor American citizens, they run up against problems due to the Constitution of the United States. They get around those legal limitations by sub-contracting the intelligence gathering, the actual data-mining, and allowing outside parties (contractors) to have access to the central database.
The government cannot conduct electronic searches (4th amendment issue) without a warrant; however, private individuals can search and report back as long as they have access. What is being admitted is exactly that preexisting partnership. The difference is that Big Tech will flag the content from within their platforms, and now a secondary database filled with the extracted information will be provided openly for the Intelligence Branch to exploit.

The volume of metadata captured by the NSA has always been a problem because of the filters needed to make the targeting useful. There is a lot of noise in collecting all data that makes the parts you really want to identify more difficult to capture. This new admission puts a new massive filtration system in the metadata that circumvents any privacy protections for individuals.
Previously, the Intelligence Branch worked around the constitutional and unlawful search issue by using resources that were not in the United States. A domestic U.S. agency, working on behalf of the U.S. government, cannot listen on your calls without a warrant. However, if the U.S. agency sub-contracts to say a Canadian group, or foreign ally, the privacy invasion is no longer legally restricted by U.S. law.
What was announced in June 2021 is an alarming admission of a prior relationship along with open intent to define their domestic political opposition as extremists.
July 26 (Reuters) – A counterterrorism organization formed by some of the biggest U.S. tech companies including Facebook (FB.O) and Microsoft (MSFT.O) is significantly expanding the types of extremist content shared between firms in a key database, aiming to crack down on material from white supremacists and far-right militias, the group told Reuters.
Until now, the Global Internet Forum to Counter Terrorism’s (GIFCT) database has focused on videos and images from terrorist groups on a United Nations list and so has largely consisted of content from Islamist extremist organizations such as Islamic State, al Qaeda and the Taliban.
Over the next few months, the group will add attacker manifestos – often shared by sympathizers after white supremacist violence – and other publications and links flagged by U.N. initiative Tech Against Terrorism. It will use lists from intelligence-sharing group Five Eyes, adding URLs and PDFs from more groups, including the Proud Boys, the Three Percenters and neo-Nazis.
The firms, which include Twitter (TWTR.N) and Alphabet Inc’s (GOOGL.O) YouTube, share “hashes,” unique numerical representations of original pieces of content that have been removed from their services. Other platforms use these to identify the same content on their own sites in order to review or remove it. (read more)
The influence of the Intelligence Branch now reaches into our lives, our personal lives. In the decades before 9/11/01 the intelligence apparatus intersected with government, influenced government, and undoubtedly controlled many institutions with it. The legislative oversight function was weak and growing weaker, but it still existed and could have been used to keep the IC in check. However, after the events of 9/11/01, the short-sighted legislative reactions opened the door to allow the surveillance state to weaponize.
After the Patriot Act was triggered, not coincidentally only six weeks after 9/11, a slow and dangerous fuse was lit that ends with the intelligence apparatus being granted a massive amount of power. The problem with assembled power is always what happens when a Machiavellian network takes control over that power and begins the process to weaponize the tools for their own malicious benefit. That is exactly what the installation of Barack Obama was all about.
The Obama network took pre-assembled intelligence weapons we should never have allowed to be created, and turned those weapons into tools for his radical and fundamental change. The target was the essential fabric of our nation. Ultimately, this corrupt political process gave power to create the Fourth Branch of Government, the Intelligence Branch. From that perspective the fundamental change was successful.
♦ WHAT NOW? There is a way to stop and deconstruct the Intelligence Branch, but it requires some outside-the-box thinking and reliance on the Constitution as a tool to radically change one element within government. In the interim, we must remain focused on the three tiers that we need for success.
• Tier One is “tactical civics” at a local level. Engaged and active citizen participation at the community, city, town and hamlet level of society. This is what might be described as grassroots level, school board level; city council level; county commissioner level.
• Tier Two is “extreme federalism” at a state level. Engaged and active citizen participation through your State House and State Senate representative. This is state level assembly and action demands upon the State House, State Senate and State Governor.
• Tier Three the challenge of “federal offices” on a national level {Go Deep}. This is the part where we need President Donald Trump, and his power to confront the issues comes directly from us.
I am confident that ultimately “We The People” will win. How we can execute the solution is more challenging; in the interim, tactical civics and extreme federalism are doable right now, in this next 2024 election cycle.
It sucks that a UniParty congress extended FISA-702. However, even if the hail-Mary pass on Monday fails, FISA was still extended for only two-years.

De Oppresso Liber
A group of Americans united by our commitment to Freedom, Constitutional Governance, and Civic Duty.
Share the truth at whatever cost.
De Oppresso Liber
Uncensored updates on world events, economics, the environment and medicine
De Oppresso Liber
This is a library of News Events not reported by the Main Stream Media documenting & connecting the dots on How the Obama Marxist Liberal agenda is destroying America
Australia's Front Line
See what War is like and how it affects our Warriors
Nwo News, End Time, Deep State, World News, No Fake News
De Oppresso Liber
Politics | Talk | Opinion - Contact Info: stellasplace@wowway.com
Exposition and Encouragement
The Physician Wellness Movement and Illegitimate Authority: The Need for Revolt and Reconstruction
Real Estate Lending
"Feel free to associate..."